Crypto Opsec: Browser (in)security to security
For the context of this post, I will be using the Chrome browser to illustrate my point. Many of these points can be applied to other browsers and I am not going to dive deep into browser wars which is meaningless. What is more important is understanding your browser insecurity or security and how to harden your opsec.
Note: This is not meant to be a comprehensive checklist.
Let’s look at my browser
So this is your browser. Which part of it can you trust and which part you can’t trust?
Let me repaint it.
Simple color representation
Green - Trusted*
Orange - Depends. Trust it partially
Red - Cannot be trusted
Are you shocked that more than 90% of your browser surface area cannot be trusted? You shouldn’t be. Browsers are meant to serve out content created by humans. Just like humans, content created can be harmful or good.
Green zone
This is the zone you can trust. This is where you can do operations like minimize, maximize, close the browser and enter URLs or search for terms. Pretty simple operation.
There are times when you cannot trust the green zone, such as
your browser has been replaced with another malicious browser
the browser team is malicious
certain flaws such as Punycode attack
CA cert compromise
But that is out of the scope for now. Such browser level flaws, if severe enough, are generally quickly patched up by the browser team.
Orange zone
This is the zone where you should start to exercise caution. This is where your extension lives.
Extensions can interact with you like how a webpage interacts with you. It can ask for sensitive data. It can modify or redress your webpage. It can even send and receive data. They are essentially like a webpage.
Do not panic yet. Many of the uses cases make sense.
If you install a crypto wallet like Metamask and use a hot wallet, it may ask for sensitive information like your mnemonics.
If you install an ad blocker, the ad blocker may redress your webpage to remove ads.
If you like dark mode and install a dark mode extension, it may redress your website to turn it into dark color.
If you want to know the latest Ethereum gas price, you may want to install an extension that often sends and receive the latest gas price information. (Btw RIP gasnow. Although short-lived, you are fantastic.)
However, with great power come with great responsibility.
So it is crucial to install the correct extension and not some fake one. As a simple rule, always download the extension from the official store, e.g., Chrome Web Store. Beyond that, check who is the developer of the extension. If you feel something is wrong, do not install it.
Also, it is crucial that you do not enable “Developer mode” unless you know what you are doing. Turning it on allows you to install an extension, not in the store. This is dangerous. The attacker may use social engineering attack to trick you into installing an extension not approved by the Chrome store.
To check whether you have developer mode enabled on Chrome, type “chrome://extensions/” in the search bar and check the top right-hand corner.
Red zone
This is where the crazy shit happens. In Runescape, you can imagine it as the wilderness. In other games, you can imagine it open area for PvP. You can lose anything here. Your cryptos, your identity, etc. This is where most attackers stage their attack.
Crypto scam DB has some examples of it. At this stage, I think I don’t need to explain in great depth what all these sites contain. 2 simple words - Phishing websites.
Crypto wallet login pop-up
What I want to warn you about is pop-up notifications like this.
This is very common. If you are logged out of your crypto wallet, the dApp, e.g., Uniswap, Aave, will prompt you to re-login again. These are typically fine.
However, this is classified under RED ZONE. This means whatever you type can be stolen if you access a malicious webpage. One common tactic is to prompt you that this is an invalid password and ask you for your mnemonics phrase to reset your password. If you have done that, it is game over.
What is recommended is - Click on your Metamask wallet extension (or other crypto wallets) and log in from there.
This will be much safer! Simple? Now start practicing it.
Phishing link masquerading as an advertisement
We like to Google. The whole world like to “Google”. When you want to access a webpage such as Uniswap or Pancakeswap, a straightforward way is to Google it. After all, Google is our best friend, right?
Think again. Google sells ads on their search. Human, good or bad, controls ad contents. Same story. It is another attack surface.
Check out this video by Check Point Research.
I also recommend you to read their article “CPR alerts crypto wallet users of massive search engine phishing campaign that has resulted in at least half a million dollars being stolen.”
A straightforward countermeasure is to use an adblocker. I will elaborate more in the later section.
Other defensive mechanisms
The following mechanisms may be specified for Google Chrome.
Safe browsing
Google Chrome has “Safe Browsing” with different tiers of protection. You may want to choose “Enhanced protection”. Again, it is a trade-off between security and privacy.
You can access it via “chrome://settings/security”.
Browser profile
Chrome allows you to have different browser profiles. Each profile feels like you are using Chrome on another machine. Extension installed on one profile cannot be accessed from the other profile. So are browsing history and other information.
So what is so useful about it. Creating multiple profiles, e.g. crypto trading, DeFi, NFT ape profile, work, personal, etc., can compartmentalize your activities and when there is an attack, it can limit your blast radius and limit the compromise.
Adblocker
(I can hear all the fans of brave browser start shouting use Brave. But let’s be browser-agnostic here).
Adblocker, block ads. One side effect is that it also blocks scam ads. There are many adblocker out there, but one of my favorite ones is Adblock Plus. Just choose the one you can trust and feel comfortable with. Do note that adblocker may come with some privacy issues, but that is out of the scope of this post. If you are concerned about it, research deeper into it.
Adblocker like AdBlock Plus, may also come with “Acceptable Ads“ as a mechanism to earn revenue from ads. Irony? Yes. To be on the safer side, disabling it might be a better option. If you appreciate the work done by your ad blocker, you can donate to them instead.
Update: Many of the readers also pointed out uBlock Origin as a good ad blocker.
PeckShieldAlert Chrome extension
Recently, PeckShield has released a new chrome extension that will warn you if you visit any known phishing site.


You can get it over at https://chrome.google.com/webstore/search/peckshieldalert
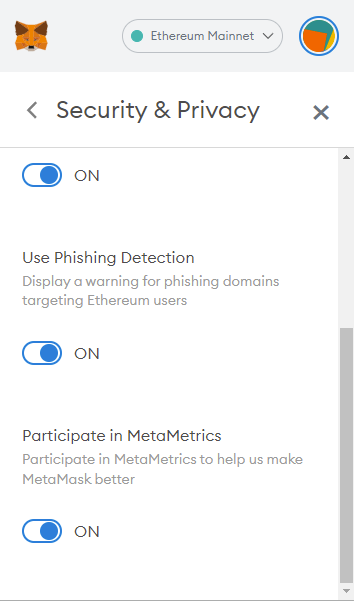
Phishing detection by Crypto wallets
Wallets like Metamask also have in-built phishing website detection. It should be enabled by default. If not, you can go to “Settings > Security & Privacy” to enable it.
One last thing
There is nothing called absolute security. If someone tells you that, it is snake oil.
What is important is that you 1) layer your security defense with different toolings in different contexts and 2) Be extremely vigilant, You are not too poor to be hacked.
Credit to Madhav for the awesome banner